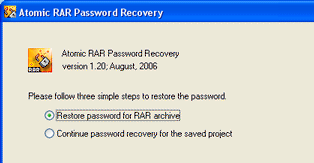
- Beginning with the first step you need to choose either to restore the password for the rar file or you can continue search for the saved project.. if you choose continue ... > you choose the saved project and the Atomic RAR Password Recovery will continue the search... If you choose Restore password for RAR Archive > a new page will appear......
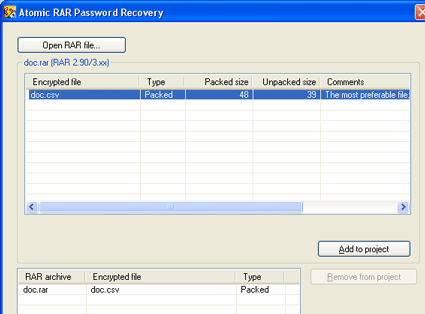
2. Now you have to choose a password protected RAR file and you have to choose the packed document to attack..
for this ,
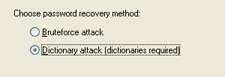
3. Now choose a way to crack the password (Dictionary attack or Brute-force attack)
- Press Open RAR File... finding your archive,
- Then the contents of that will be shown. - Use Add Project Button
- Press NEXT to choose a password recovery method..

3. Now choose a way to crack the password (Dictionary attack or Brute-force attack)
In the Dictionary Attack, Atomic Password Recovery will load the available password from the dictionaries provided...
In the Bruteforce Attack, the program will automatically generate a list of all the available passwords.... The password will be checked to the correctness. You will find it to be the slowest method of Password finding , but you can use this option if everything fails.......
4. Dictionary or Bruteforce attack :-
- In DICTIONARY ATTACK...
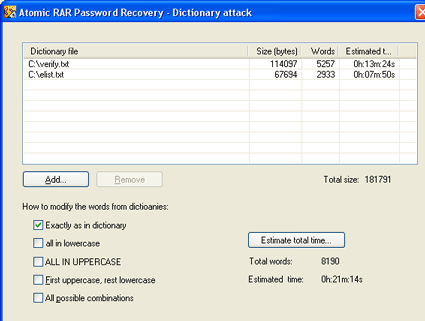
In this method you will be needed to provide with one or more files with words to verify. Atomic RAR Password Recovery will check all the provided words. you may also modify the loaded words :-
- ) all in lowercase (WORD>word)
- ) ALL IN UPPERCASE (word>WORD)
- ) First UPPERCASE , rest lowercase (WORD or word > Word)
- If BRUTEFORCE ATTACK...
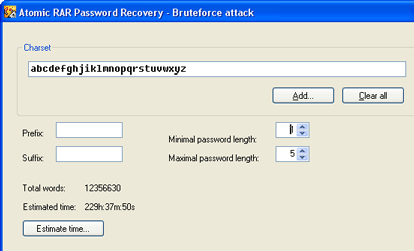
You need to specify the limit for generating password list. you can define the charset ; minimal and maximal length of the generated passwords...
PREFIX and SUFFIX- you may add signatures to the passwords here...
5. Checking the Password :-
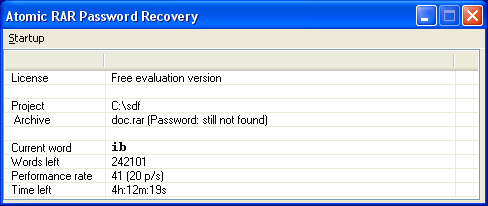
In this step the application will check the available passwords one by one , and will inform you about the process..... you may pause or terminate the search.. If you pause , you can continue the search later......
No comments:
Post a Comment